These videos explain basic network security functions, and how you can deploy them to provide foundation level security for your network. Each video will enable you to enhance your knowledge of a specific aspect of network security.

Part 1: Introduction
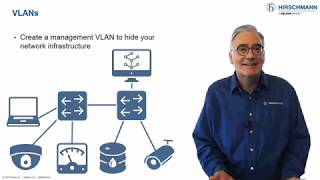
Part 2: Protecting Your Network Infrastructure
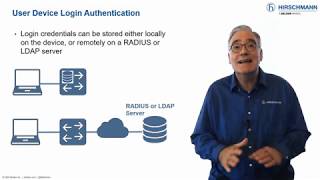
Part 3: Protecting Your Network Infrastructure Interaction
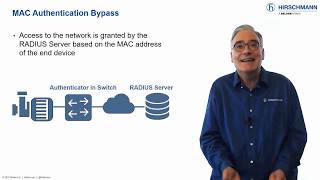
Part 4: Enforcing Network Access Policy

Part 5: Deploying Access Control Lists

Part 6: Controlling Malicious Traffic
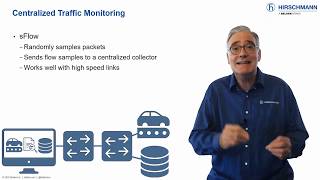
Part 7: Logging Security Events

Part 8: IEC 62443 - Independent Certification

Part 9: Conclusion – Next Steps
-
Part 1: Introduction
These videos explain basic network security functions, and how you can deploy them to provide foundation level security for your network. Each video will enable you to enhance your knowledge of a specific aspect of network security. Presented by Mark Cooksley. #PlainlyExplained -
Part 2: Protecting Your Network Infrastructure
The first step on your security journey should be to protect your network infrastructure itself. With a few simple actions you can regulate access to your network devices. Presented by Mark Cooksley. #PlainlyExplained -
Part 3: Protecting Your Network Infrastructure Interaction
Presented by Mark Cooksley. #PlainlyExplained -
Part 4: Enforcing Network Access Policy
The next step is to decide which devices and which people are allowed to communicate on your network. If you restrict network access to authorized users, you greatly reduce the opportunities for an outsider to attack your operation. Presented by Mark Cooksley. #PlainlyExplained -
Part 5: Deploying Access Control Lists
Access Control Lists allow you to permit and deny traffic transmitted into or out of network interfaces, based on a range of criteria. Presented by Mark Cooksley. #PlainlyExplained -
Part 6: Controlling Malicious Traffic
Denial of Service attacks can cause a production failure and therefore financial loss. Various techniques are available to prevent disruption to your network communication caused by malicious data traffic. Presented by Mark Cooksley. #PlainlyExplained -
Part 7: Logging Security Events
Log files provide a record of activity which can help you to understand what took place in the past. This will allow you to detect threats and respond to security concerns. Presented by Mark Cooksley. #PlainlyExplained -
Part 8: IEC 62443 - Independent Certification
IEC 62443 provides a certifiable framework to address security in Industrial Automation and Control Systems, across all industry sectors and critical infrastructure. Presented by Mark Cooksley. #PlainlyExplained -
Part 9: Conclusion – Next Steps
Implementing network security is a process, not an action. It will happen over time. At this point you can now evaluate where you see the greatest threats to your Ethernet network. Presented by Mark Cooksley. #PlainlyExplained
